Heimdal Thor Enterprise and Emsisoft AntiVirus – AntiMalware deliver the ONE- TWO PUNCH KNOCK OUT PUNCH COMBO
The ProActive:
Heimdal Security – Since 2011, has been leading the fight against cybercrime, developing new technologies and providing intelligence to protect over 5,000 companies and 600,000 users against cybercriminal attacks and data security breaches.
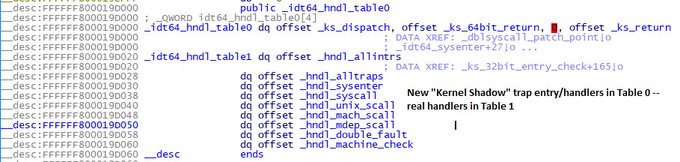
With security Products for Home and Business , Heimdal security takes a Proactive approach to securing your data. With the complete pack THOR Premium your endpoints are SAFE! unlike traditional Antivirus products Heimdall’s complete package with Thor Premium sits basically at the network card level and is constantly scanning incoming and outgoing traffic, Your DNS is pointed to the Heimdal Security centers robust network, and traffic is scanned at the network level. By scanning through the network connection Thor can stop, block and cease an attack before it reaches your machine, since it is done in route through a highly secure DNS server. The complete Business package allows for updating 3rd party applications and Windows security patches automatically closing loophole and breaches due to unsecure or unpatched software. Automatically scheduled scans of your files and constant scanning of incoming and outgoing data and where they are connecting ( endpoints). Is your online application really connecting to say your bank or has it been hijacked and pointed to a dark web or malicious hackers page masking itself as the real deal only to steal your data?

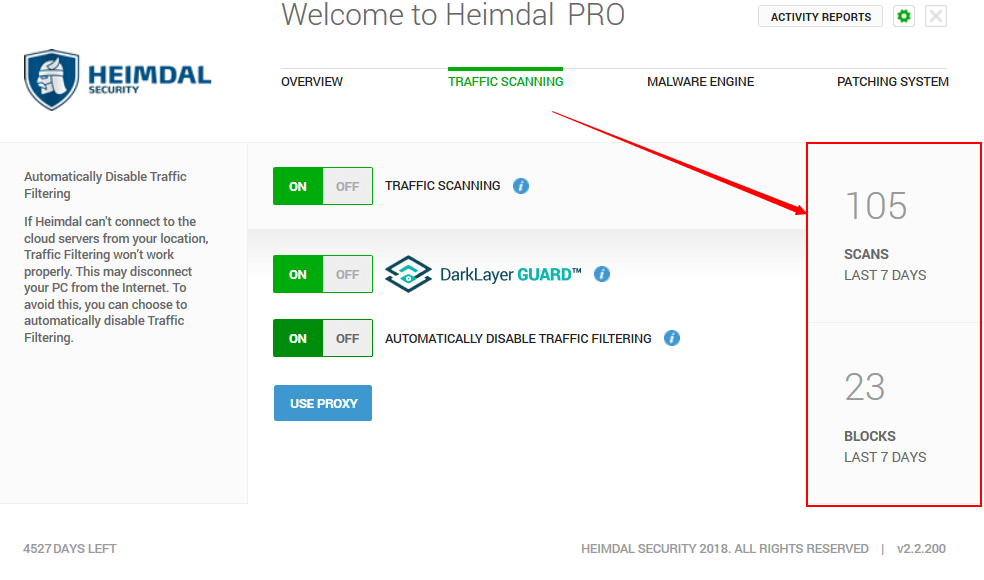
Detects threats at the DNS, HTTP, HTTPS layers, before they reach your device, and prevents data leakage and compromise. With a unique, proactive approach to security, DarkLayer Guard™blocks all incoming and outgoing communications to malicious servers, preventing APTs and other threats.

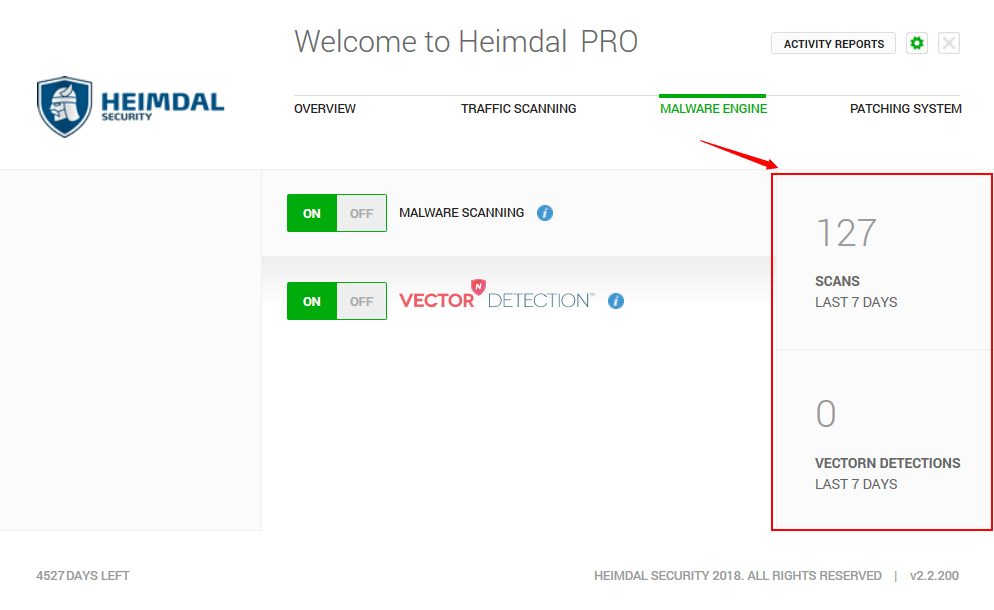
While antivirus is a reactive solution that scans code to stop threats, our VectorN Detection™ will autonomously detect and prevent infections.
Through VectorN Detection™, hidden malware in your system will be immediately detected and blocked before it can compromise your data.
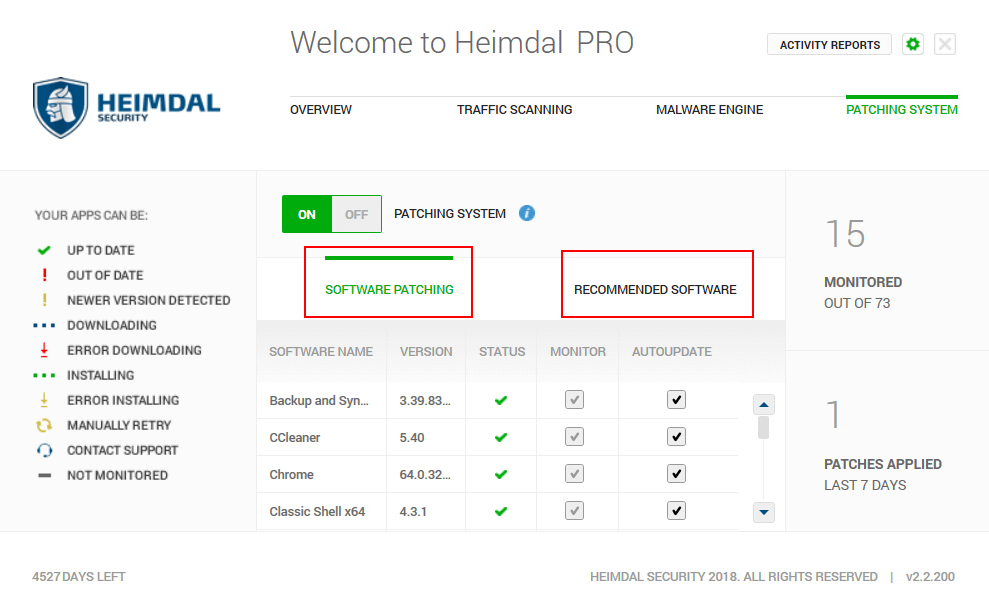
Through X-Ploit Resilience, available updates are automatically and silently updated. This way, you eliminate vulnerabilities before they’re exploited AND infect your PC with malware. Windows Security Pacthes and updates are applied on a scheduled basis along side many 3rd party applications, Updates to these application is patched automatcially when a new patch or update is available it will automatically be installed with the least amount of user intervention.
The Reactive:
Forget viruses – Today’s threats come in new shapes and are called Malware
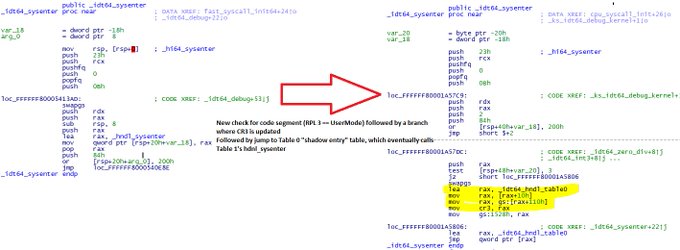
Emsisoft’s high performance dual-engine scanner
Emsisoft not only detects more because it uses the full power of two major antivirus- and anti-malware technologies, it also scans quicker because of the efficient combination of the scanners.
Any unnecessary duplicates in detection are avoided, enabling the least impact on memory and overall hardware resources.
The engine Emsisoft has built complements the second Bitdefender engine, and they are combined seamlessly to maximize efficiency.
One of the ways they detect unwanted programs is through signature-based detection. What this means is that we search programs for their unique signatures, which are like fingerprints, and scan your computer for these threats. At Emsisoft, most of there lab time is spent creating detection signatures for PUPs (potentially unwanted programs) and on custom malware removal code for specific infections. We ran some numbers a while ago and discovered that more than 74% of the total detected PUPs are detected by our in-house built scan engine component.
So how does information translate to your own practical use?
Simple: all detections with an (A) postfix are from our own engine and those with (B) are from Bitdefender.
In a nutshell: We believe two engines are better than one, and we use our own technology to detect threats to your computer that might otherwise be missed. But we won’t compromise efficiency in this process — Emsisoft works to keep your memory clean and uncluttered, and to detect threats at optimal speed.
For the last 4 months I personally have been running Heimdal Thor Enterprise alongside the trusted Emsisoft antivirus, and feel this is the ULTIMATE SECURITY / Antivirus-Antimalware combination available by having an Reactive and Proactive software suite I feel confident my data is secure, and any internet sites I visit or use are not sneaking in backdoor threats or phishing, or worse parading themselves as the real site only to be fake and stealing any data they can get ahold of. Last thing I want to do is come home and have to clean up my own systems or laptops which is why I run both Heimdal and Emsisoft on every machine I use for the business and computer in our home. I won’t sell something I personally don’t use, and I won’t sell something which doesn’t work!
Contact RSL Computer Solutions, today and get the ONE-TWO Punch Advantage! Heimdal and Emsisoft the deadly One-Two Punch combo against Malware, Ransomware and Malicious Attacks!
Phone: 513-816-1344 or Email: Info@rslcomputers.com